21.10.2024
How Keycloak simplifies authentication and authorization: A look at the most important functions.
IAM simple and secure? Keycloak helps you.
In our digital world, secure authentication and authorization mechanisms are an absolute must. And exactly here comes Keycloak into play – the Open-Source wonder weapon that enables companies and developers to juggle users securely and provide them with frictionless access to applications. In this article, we will take a closer look at Keycloak, explore its most important functions and show you through a practical example how you can integrate Keycloak into your project in no time.
Introduction
In today's digital world, secure authentication and authorization procedures play an increasingly important role. Precisely here, Keycloak comes into play – an Open-Source solution that enables companies and developers to manage users securely and offer seamless login processes. But what exactly is Keycloak, and why should you use it in your company or project?
What is Keycloak?
Keycloak is an Open-Source Identity and Access Management system that supports Single Sign-On (SSO), User Management and integration with various Identity Providers. With over 23,000 stars on GitHub, Keycloak is one of the most popular Open-Source solutions for authentication and authorization. It enables users to securely connect to various services without having to enter their login information each time. Keycloak simplifies the user experience and simultaneously offers security by handling complex authentication procedures like OAuth2, OpenID Connect or SAML.
Why use Keycloak?
Implementing authentication and authorization can be challenging and time-consuming. Keycloak takes this burden off developers by offering a simple and high-performance solution that can be seamlessly integrated into various systems. Through functions like Single Sign-On, User Role Management and Multi-Factor Authentication (MFA), Keycloak enables combining security and user-friendliness.
For companies, using Keycloak means not only increased security but also significantly reduced development time for security-critical functions. Simultaneously, Keycloak can be easily scaled to keep up with growing user numbers.
Keycloak in Practice
Integration into Existing Systems
Integrating Keycloak into existing systems is uncomplicated, as it offers flexible API interfaces and can be easily integrated into frameworks like Spring Boot, Django, Node.js and many other technologies. Whether you operate a cloud-based infrastructure or on-premise systems, Keycloak adapts to your company's requirements. Thanks to its Open-Source nature, it is also completely customizable. For example, we created a Cookie-Cutter Template for easy customization of the Keycloak theme.
Practical Example: FondsFinanz Broker Educational Platform
A concrete example of a successful implementation of Keycloak is the backend world of the FondsFinanz Broker Educational Platform, a Django-based Kubernetes application with various services. Here, a central Keycloak instance manages authentication for all services and ensures uniform and secure user management. This setup enables a seamless and secure user experience.
Hereby, pycloak plays a significant role. Through pycloak, we could seamlessly integrate Keycloak into the Django application via the oauth2-proxy project.
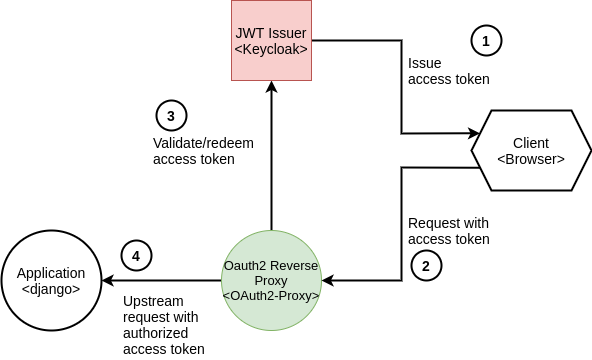
The above image shows the flow of how pycloak implements authentication via the oauth2-proxy in the Django application. The client application first navigates to the desired resource and is intercepted by the oauth2-proxy. This redirects (if the client application is not already authenticated) the user to the Keycloak login page. Here the user must authenticate and can subsequently access the desired application with the provided access token.
Practical Example: LUMA Delicatessen
Another example is the LUMA Delicatessen-Website, based on Nuxt.js and Django. Here Keycloak is also used as a central authentication solution to ensure security and user-friendliness. For example, we have adjusted the registration page and standard Keycloak fields using our keycloak-theme-template. Among other things, the question about the date of birth was added to enable potential discount actions. The entire look then appears like this:
Practical Example: LMU Munich Media Monitoring
Keycloak also offers an API that we use for the Munich Media Monitoring at LMU to retrieve user accounts for re-verifying their email address after a certain time. With the User Profile function of Keycloak, we have added additional fields to the user accounts to mark when a user must re-verify their email address. A Kubernetes Cronjob communicates with the Keycloak API to precisely identify these users and send a POST request via the Keycloak API to trigger the email verification. If one of these users subsequently uses the Munich Media Monitoring, the automatic request from Keycloak to verify the email address is triggered.
Advantages for Developers and Companies
Keycloak offers numerous advantages, both for developers and companies:
- Time Savings: Developers no longer need to deal with the implementation and maintenance of authentication and authorization logics.
- Scalability: Whether you have a small application or a large company, Keycloak can grow with your requirements.
- Flexibility: Thanks to support for various authentication standards, Keycloak can be connected to numerous systems and applications.
- Security: With features like Multi-Factor Authentication, Password Policies, and role-based access control (RBAC), Keycloak offers a high security level.
Why Choose Blueshoe as a Partner?
Bluesho has established itself as an experienced partner for Keycloak implementation and offers pycloak as a tailored solution for Python-based applications. Pycloak is a package that enables developers to seamlessly integrate Keycloak into Python projects. Through this development, Bluesho has succeeded in making Keycloak even more accessible and adaptable for developers. With the latest version (as of October 2024), there is now also official support for Python 3.12 and some improvements to the logs() function!
If your company is looking for a flexible and secure authentication and authorization solution, Bluesho not only offers technical expertise but also tailor-made solutions like pycloak to successfully shape your project.
Conclusion
Keycloak is a fantastic open-source tool that brings security and user-friendliness into harmony. Whether you're looking for a simple SSO solution or need to manage complex user roles – Keycloak has you covered.
When you are looking for a professional implementation of Keycloak, contact the Blueshot team. We help you integrate Keycloak into your system and offer tailored solutions to meet your security requirements. Get non-binding advice now!
Do you have questions or an opinion? With your GitHub account you can let us know...




